-
FORESTIER Fabien authoredFORESTIER Fabien authored
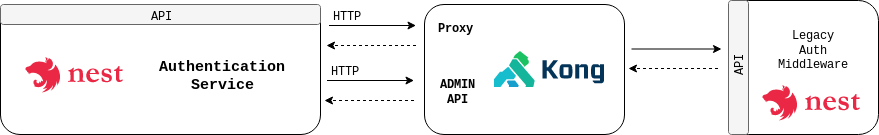
Authentication service
Features
This service allows users to login to / logout from the Web Portal. Establishing an authenticated session is a prerequisite for managing user rights to restricted-access resources.
Dependencies
The service relies on
- the API Gateway, in particular its Admin API;
- external identity providers, which actually store user profiles and can verify user credentials. Despite being designed to potentially support different identity providers, in the present implementation only the Legacy AUTH Identity Provider is supported. A middleware was developed, so as to facilitate the interaction between this service and the Legacy AUTH Identity Provider.
Endpoints
This service provides five endpoints:
-
A login endpoint per identity provider (just one in the present implementation, namely
/login/legacy), allowing users to authenticate using a username/password pair. In case the identity provider confirms that user credentials are correct, a couple of cookies are set:- an HTTP-only cookie including an access token, including in turn a JSON Web Token (JWT), signed by the API Gateway, namely Kong.
- a cookie including an XSRF token (generated as a version 4 UUID).
Both the access token and the XSRF token are needed to issue authenticated requests. We refer the reader to a dedicated page for further information about security.
-
A logout endpoint,
/logout, which signs out the user by deprecating the cookie set by the login endpoint. -
An user info endpoint, allowing one to fetch an user profile.
-
An user info update endpoint,
/user/updateallowing one to update an user profile. -
An health endpoint,
/health, returning a200HTTP Status Code in case the service is healthy,503in the opposite case. For this service to be healthy, two conditions must be fulfilled:- the API Gateway must be up;
- the Legacy AUTH Middleware must be up.
Implementation
The service is implemented using the NestJS framework. We refer the reader to the NestJS-based micro-services page for further details concerning the latter framework and the features it provides.
TO FURTHER DEVELOP
- What's the interplay between this service and Kong? Let's provide sequence diagrams!
- How is the access token generated and signed?
- What is the difference between the cookie expiration time and that of the JWT for the Legacy Middleware?